-

No, server hardening does not mean you need to replace your server racks and cases with tempered steel. Hardening refers to the process of increasing security and decreasing the attack surface of a device, making it harder to attack and more resistant to damage if it’s attacked.
The process of server hardening involves going through a lot of different subsections of your IT infrastructure, to make sure they’re secure, implement better security where they aren’t, identify flaws and vulnerabilities, and generally lower the attack surface. This can involve:
-
- Changing account defaults and removing guest accounts and access.
- Turning off subsystems, scripts, drivers, and other features that aren’t necessary.
- Updating software to ensure known bugs and exploits are patched and fixed.
- Configuring timestamps to ensure continuity between devices and across the network.
- Minimizing open ports, and locking down access via open ports.
- Locking down RDP and other remote access channels.
- Taking additional steps to harden any applications in use.
- …and much more.
Needless to say, this is the realm of the specialist. It’s a deep and complex task that requires dedicated knowledge of common and uncommon threats, vectors of attack, and how to take action to harden an infrastructure regardless of what that infrastructure contains.
If you’re looking to hire someone to handle your server hardening, you’ll need to figure out exactly what you need and how to get it. Think about these topics to give you an idea of where you stand and what you need to do.
Determine the Scope of Your Needs
Different businesses have different configurations and thus have different needs. A small business with largely cloud-based tools, a simple web server with VPN access to keep it secure, and data entirely stored on network drives and not local drives has a relatively low attack surface. A multinational corporation with offices in a dozen countries, a hugely disparate set of infrastructure hubs, and more communications channels than you can count, will have a much greater need for attention and compliance.
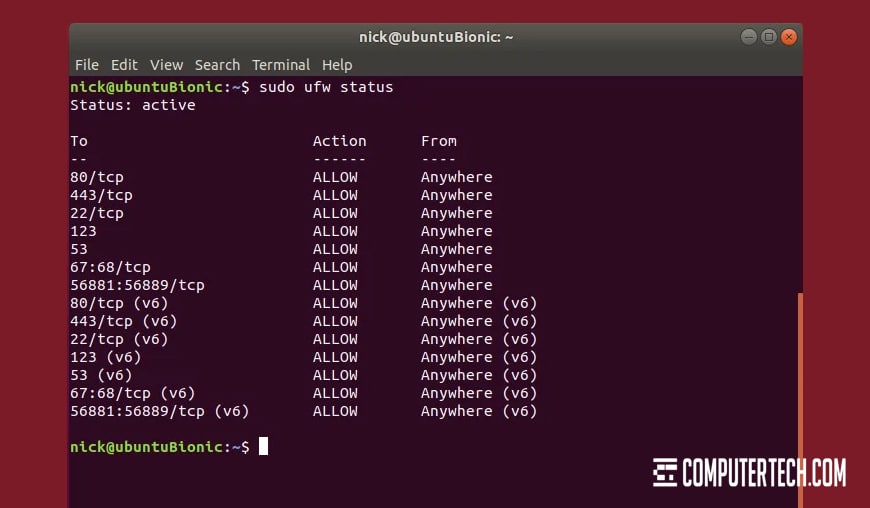
You’ll need to put together an idea of what your contractor will be working with. Are you using a Windows-based infrastructure, or Linux-based, or a hybrid system? Do you have a small handful of web servers or a lot of them? Do you keep everything in one central HQ, or do you have different infrastructures for different offices?
One crucial question you’ll need to answer is whether or not you’re in a position to need specific compliance. For example, if you’re a merchant dealing with credit card data, you will need to be PCI-DSS compliant. Other companies may need to comply with the ISO27001 security standards instead, or in addition to, PCI.
In general, the more hardware you use, the more software you use, the more people you have using it, the more locations you have accessing it, and the more data you store, the more attention will need to be paid to security.
Consider Any Past Attacks
If your company has been the victim of any digital attacks in the past, you’ll want to keep that in mind when you discuss the subject with a contractor or company you interview to do security and hardening for you.
DDoS attacks – Dedicated Denial of Service – are some of the most common forms of digital attacks out there. They can take down a website, shut down a business, and expose vulnerabilities that can be accessed in other ways.
Other forms of attack are more insidious, harder to detect, and occasionally even invisible without monitoring access logs. While they might not have an immediate impact on your business, they are potentially much more damaging, with loss of customer data a primary concern.
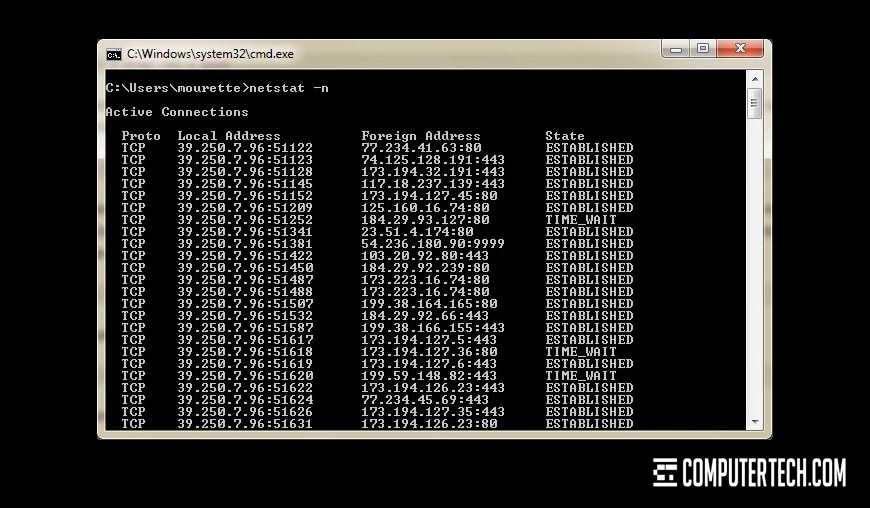
A server hardening process can protect against most threats, though no system is perfect. However, knowing what sorts of attacks have happened before, and what their results were, can help inform a contractor what they’ll be working with.
If your company hasn’t been the target of an attack in the past, great! That doesn’t necessarily mean your security is good. In many cases, it’s only a matter of time before someone turns their attention your way. You want to be hardened before that happens.
Drop the idea of security through obscurity. Far too many business owners think that, just because their business is small or their infrastructure is light, they’re safe. “After all, who would even think to look? We don’t have enemies.” This kind of thinking doesn’t matter. There are people who create bots that systematically check IP addresses for vulnerability, regardless of what they are. Just watch a video like this and you can see just how vulnerable you can be when you think you’re invisible. Obscurity is not security.
Be Willing to Implement Solutions
Regardless of who you hire to handle server hardening and security for your company, you need to be willing to make changes and implement solutions. All too often, a business will hire a contractor to handle server hardening, only to hobble them with a lack of budget, access, or policy change.
Security involves more than just server configurations. A lot goes into it, and some of it will involve changes you might not want to make.
- Configuration changes. These are easy. Tweaking settings on a server, tightening down a firewall; most of this isn’t even noticeable by your employees. Some, though, will, like disabling shared accounts and guest access.
- Policy changes. In some cases, you will need to implement rules about browsing websites from work devices, about accessing and sharing user accounts, and all manner of other behavioral restrictions. These changes need to be implemented from top to bottom; your C-levels are not exempt because they’re at the top of the food chain.
- Hardware changes. In some cases, old hardware may not be salvageable as a secure device. In other cases, you may need to be willing to implement something like a hardware firewall to provide an additional layer of access control, intrusion protection, filtering, and logging.
- Access changes. One key change many businesses need to make is removing admin privileges from virtually everyone in the organization. A huge number of intrusions, crypto locker attacks, and other infections come from allowing non-IT employees admin access to install programs. Another change may involve removing access, by making a VPN standard and removing other (potential less secure) channels.
Whoever you hire to harder your system needs to be given access to make changes, which means full “super admin” access, or root access, to your infrastructure. They can be supervised, of course, but if you hamper their ability to perform their tasks, you’ll end up with a less secure system.
Determine Whether You Need a Contractor or a Company
The biggest decision you’ll need to make is determining whether you need to hire an individual consultant to come in and fix your security, or if your needs are such that you need to work with a company that brings a team along with them.
Individuals tend to be cheaper and may be easier to work with. Some individuals may have more familiarity with your business or with your industry. If your systems are relatively slim, you don’t have any major issues that need to be addressed, or if you’re operating on a shoestring budget, working with an individual security specialist is likely the best option.
On the other hand, there are a lot of reasons it might make more sense to go with a security firm to handle your hardening.
- Your company is large enough and your infrastructure disparate enough that one person can’t cover it all.
- You have unique or specialist concerns, such as PCI compliance, HIPAA compliance, or other industry-specific issues.
- You have an audit coming up and need to get your security in place quickly, which may require a team working on it rather than an individual.
- You’re skeptical of the quality of individual contractors. (Companies tend to be more visible, have more public reviews and information about them, and build reputations more than individuals.)
Most of the time, we would recommend working with a company unless your needs are very low, you need a review and update to already-secure systems, or you know of an individual with an exceedingly good reputation you can hire.
How to Hire a Specialist for Server Hardening
All of the above leads you to what is essentially the first step of hiring someone to harden your infrastructure: determining your needs, requirements, budget, and desires. Figuring out the scope of what you need allows you to start researching consultants and firms you can work with.
Once you have an awareness of what you need, you can start building a list of possible consultants to hire. You’ll have access to both local and national firms. Local firms are likely going to have less exposure, lower prices, and more familiarity with your brand. On the other hand, they might not be as trustworthy or as reputable as larger companies, and they might not always provide the best service. National firms can work with you from anywhere, but will likely be correspondingly expensive. There’s also no guarantee that they’re any better than a local company.
If you have specific needs, like ISO or PCI compliance, you’ll need to filter your list of potential consultants to find only those who are certified and experienced in that kind of compliance.
Once you have narrowed down your list, it’s time to start contacting them and interviewing them to see if they fit your needs. Here are some questions you can ask them to get a feel for this fit:
- How much do they cost?
- How long will the hardening process take?
- Have past clients been attacked, and how did they handle it?
- Do they provide continual support and reviews periodically?
- Can they explain the basics of PCI compliance?
- What do they consider the most important part of server hardening?
These questions, and their responses to them, will give you a basic idea of the quality of the people you’ll be working with. Most of the time, any company you find that isn’t a new startup or unknown name will be perfectly acceptable for most server hardening tasks. It’s only for the largest and most complex systems where you may need to find a custom specialist willing to work with your company.
Maintaining Security
Remember: security is not a one-time thing. You need to continually comply with policies, harden new surfaces, and keep your systems up to date.
Make sure policies are being followed through regular checks. One of the largest weak points in any system is the people involved in it. Your employees may try to find workarounds, your IT staff may compromise systems for their own purposes, and so on. Any compromise made opens up a new threat vector that can be exploited by an attacker that finds it.
Perform periodic audits to make sure configurations are still secure. Whether you do this with an internal checklist, you hire a contractor – even the same one – to come in and audit, or you hire a server security specialist to become part of your staff, you should set up routine checks to make sure compliance is maintained.
Harden any new hardware or software added to your systems, at or before the time they’re added. Whether it’s a new client PC for an employee, a new server, or even a new app you’re using as part of your business processes, it should be checked for security compliance and tweaked to fit before it’s added to your overall infrastructure.
Monitor ISO, PCI, and other regulatory bodies to keep aware of changes to the standards. This is the homepage for the ISO 27001 information security standard, and this is the home of the PCI standard. Other standards, such as HIPAA, have their own resources as well.
Monitor logging to ensure the swift detection of any intrusion. Any device that can access your systems should be logged, and those logs should be reviewed regularly. Routine review of logs, plus well-placed alarms (that avoid alarm fatigue), should allow rapid detection and response to any intrusion. Additionally, you should have a plan in place to deal with any detected intrusion, including any necessary notification and disclosure steps, investigation, and record-keeping.
Business security is serious and needs to be treated with the utmost respect. Hiring a firm to handle your server hardening is a key part of that process, but luckily it’s not as difficult as it might seem.
About The Author
Herman
Herman is the lead team member here at Computertech.com. He’s been in IT for over 20 years and has expertise in our various IT Services including Microsoft Azure, Microsoft 365, Microsoft Teams and even Computer Security.
No related posts.
-
IT Support | IT Services | IT Consultant | Computer Support
Speak to a Human (856) 347-2282
- Home
- About Us
- Services
- IT Support
- Managed IT Services
- IT Consulting and Strategy
- IT Security Services
- IT Infrastructure Services and Networking
- Help Desk and Onsite Support
- Communication and Collaboration
- Specialist IT Services
- Data Backup and Disaster Recovery
- Cloud Computing
- Optimizing Network Consulting Services
- Remote Monitoring and IT Management
- Business Computer Services and Consulting
- Blog
- Contact Us
Navigation- Home
- About Us
- » About Computer Tech
- » What To Expect
- Services
- » IT Support
- » Managed IT Services
- » IT Consulting and Strategy
- » IT Security Services
- » IT Infrastructure Services and Networking
- » Help Desk and Onsite Support
- » Communication and Collaboration
- » Specialist IT Services
- » Data Backup and Disaster Recovery
- » Cloud Computing
- » Optimizing Network Consulting Services
- » Remote Monitoring and IT Management
- » Business Computer Services and Consulting
- Blog
- Contact Us
How to Hire a Server Hardening IT Consultant to Improve Security
In need of IT Services or IT Support? Call us today at (856) 347-2282
About Us
Computer Tech is an IT Consultant \ Computer Consultant firm providing Computer Support, IT Support and IT Services in South Jersey, IT Support North Jersey, IT Services Delaware, IT Services New Jersey, Philadelphia Pennsylvania.
(856) 347-2282Get started:
Managed IT Services
Nationwide IT Support
Managed IT Support New Jersey- Pros and Cons of Outsourced SOC (Security Operations)
- How to Find and Eliminate Wi-Fi Interference in the Office
- 7 Tips to Wire Up an Office to Maximize Wi-Fi Speed
- Can You Still Recover Hard Drive Data if It’s Water Damaged?
- How New Technology Has Changed the Modern Workplace
- The Pros and Cons of Outsourcing Your IT Department
- Custom Gaming Installations for New Jersey Businesses
- Computer Installation in New Jersey – How Does It Work?
- How to Hire an IT Team to Build an Office Network
- The Benefits and Future of Remote IT Support for Businesses
Newsletter
Computer Tech, LLC.
105 Market Pl Suite 1, Glassboro, NJ 08028
(856) 347-2282
© Copyright 2025 HighTech Business Solutions. All Rights Reserved.